哈工大的校赛,抽了两个下午打了几个小时,还是菜了2333。记录一下。
MISC
BaSO4
压缩包中有两个文件,一个pyc和一个编码过后的flag文件。pyc反编译得到代码
|
|
编码20次,每次随机base32或base64。根据每次结果含不含小写字母即可判断编码类型,进行解密,python的base64库因为补位的等于号数量会报错,懒得补了直接cyberchef拖几次得到flag
攻击流量分析
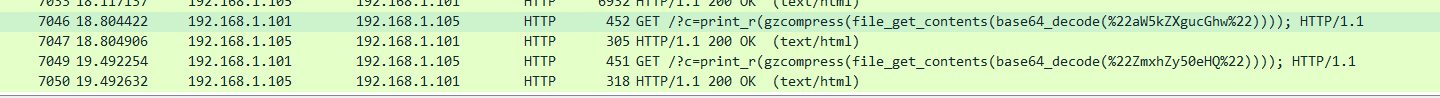
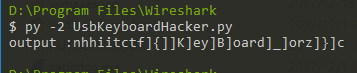
wireshark打开后过滤http肉眼即可看到明显异常的数据,第一个文件名base64解码后为index.php,第二个为flag.txt。 于是把第二个的response内容进行gzuncompress得到flag
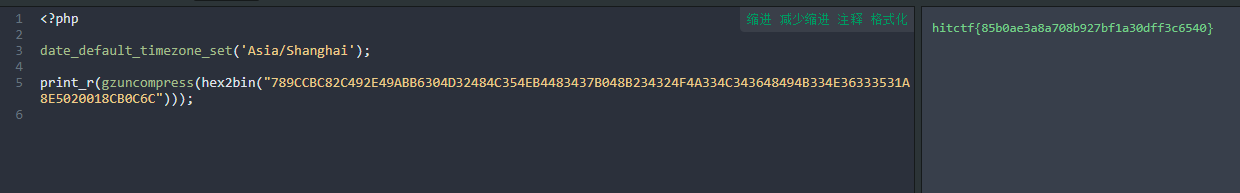
use_your_ida
这道题就非常有意思了,提供了一个超大的elf文件,ida打开后发现基本上都是没什么用的代码,只有输出一个小白羊的代码有用。
经过一番查找发现这是defcon23中写M/o/Vfuscator的大佬的其他小玩意,传送门 利用了ida的流程图传递信息,由于ida默认图形显示在函数太大时关闭,调整这个限制的大小(默认为1000)
随后看图即可得到flag

键盘流量分析
数据包中有usb键盘和鼠标的数据,先利用tshark提取数据
tshark -r keyboard.pcap -T fields -e usb.capdata > usbdata.txt
然后利用python脚本解析
|
|
忽略长度较短的鼠标数据。因为大小写所以判断一下shift状态,得到的结果稍微处理下得到flag
WEB
PHPreading
访问index.php.bak得到源码
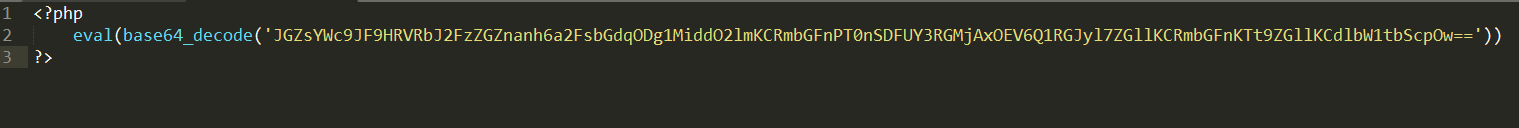
base64解码得到
|
|
按要求构造请求得到flag
BabyEval
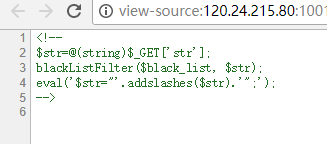
浏览源代码发现提示。利用花括号和美元符执行代码,两层来绕过addslashes,${eval(...)}让php认为里面为变量名所以不进行过滤,而再加一层又成为了字符串。因为过滤了引号,为了方便通过另一个参数传递命令http://120.24.215.80:10013/index.php?str=${${eval($_POST[c])}&c=,蚁剑连接,在根目录下找到flag文件。

小电影
ffmpeg任意文件读取漏洞,主页源码中提示了flag文件地址,利用POC脚本构造avi文件上传
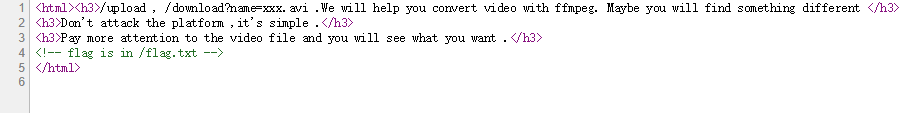
下载得到flag
SecurePY
找到了原题大佬的题解,传送门
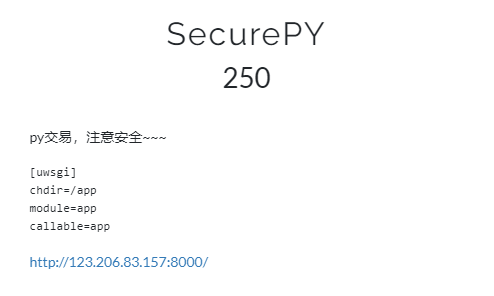
python3中__pycache__存放编译好的pyc文件,访问manage.py发现403,于是访问http://123.206.83.157:8000/__pycache__/app.cpython-35.pyc
下载到app文件,查看代码
|
|
由于其在判断两key是否相等时通过异或来对比,异或遇到null会报错,而输入又没有做过检测,所以可以通过报错来检测长度和爆破每位key
|
|
REVERSE
Baby Android
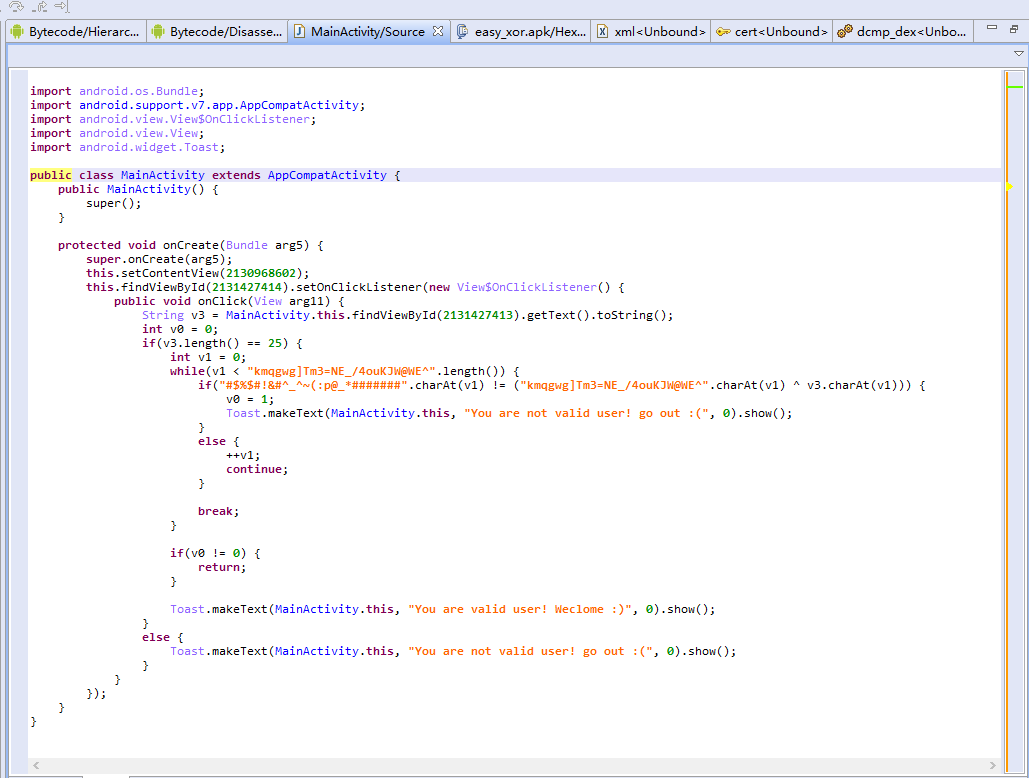
jeb打开,发现两个字符串异或,得到flag
|
|
网管的麒麟臂
给了c文件和反汇编的结果,估计之前是个pwn题改编的,直接看asm文件就行
|
|
调用了key1 key2 key3然后将三个返回值相加与输入对比。三个key两个纠结于pc,一般来讲pc应该指向下一个指令,但由于流水线(pipeline)导致其应该指向正在取址的指令也就是下下条指令而不是正在译码的下一条指令。 其中key1返回值为mov语句执行时的pc,也就是下下条指令地址0x00008ce4;key2切换为thumb指令集再执行也先取了pc值也就是0x00008d08,再加上4得到0x00008d0c;key3返回lr也就是key3函数返回地址0x00008d80,相加得到flag
学习资料的密码
将encrypt.exe用ida打开,F5
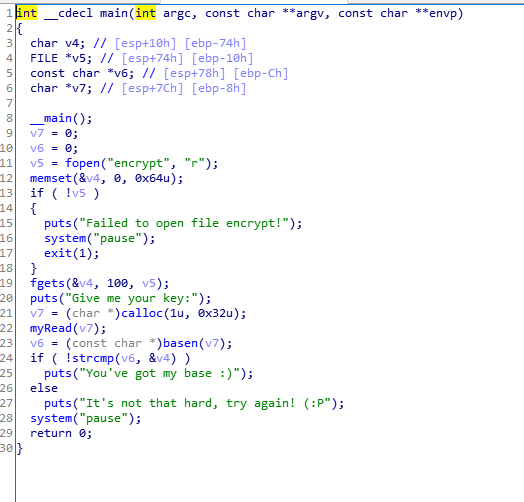
|
|
可以看出basen函数每三位一组,也就是base8,再看chart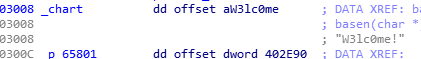
写脚本还原为二进制
|
|
即为flag
CRYPTO
单表代替
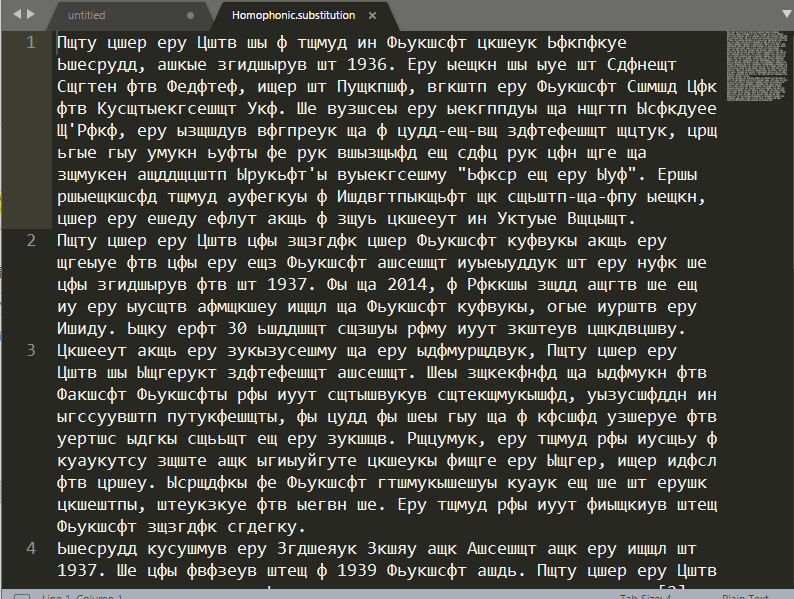
一堆俄文字母,其中可以发现标点符号和数字应该是没有替换的。由提示得到原文应为英文。根据常见英文词以及字频可以发现长得像epy的是the,同样可以看到年份前的in,一步步替换,最终得到差不多的全文,是《飘》的英文简介,维基百科查到原文,将部分未替换的出现次数较少的字母替换掉,得到flag
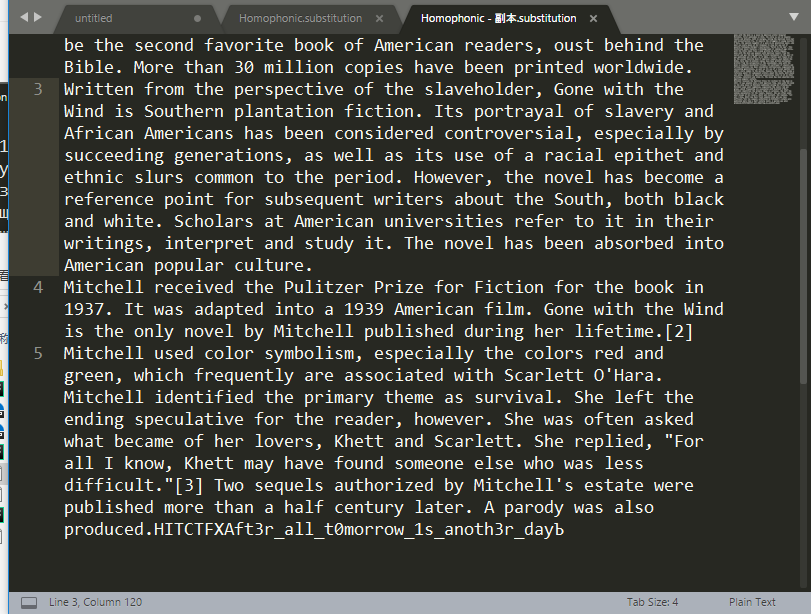
多表代替
多表替代,维吉尼亚密码,在线解密 ,出乎意料的没出问题,得到flag。
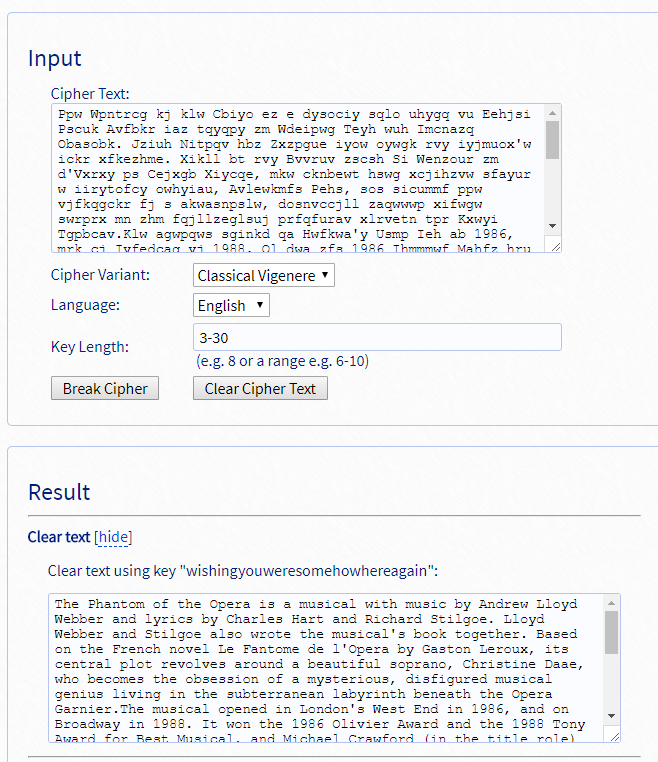
EASY_XOR
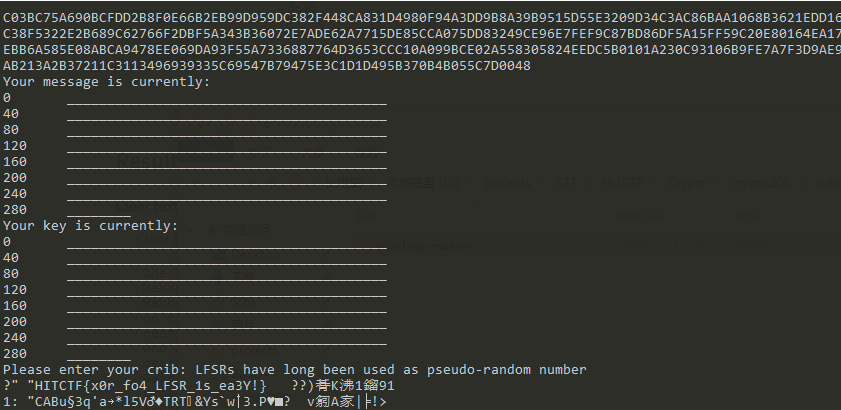
题目既给了明文也给了密文,提示其实并不需要,直接尝试cribdrag
密文输入,将明文一段当作crib得到key
PWN
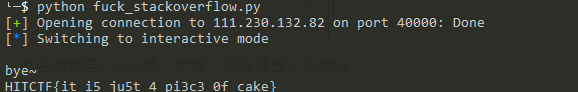
stackoverflow
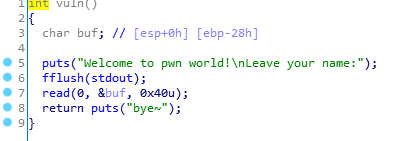
vuln中通过输入覆盖返回地址到程序内置flag函数
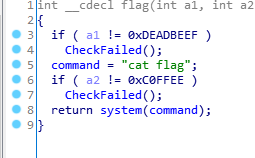
此函数需要check两个参数,同样覆盖对应地址,得到flag
|
|
总结
本来没注意到这个比赛,这校赛的质量是我们学校可望不可及的啊。不少题都挺有意思的比如杂项中的use_your_ida,我这个菜鸡也终于算是个业余pwn手比赛里做出来道pwn - -.